What exactly is a proxy server and what benefits can it offer? Let us first comprehend what an IP address is and what it is used for on the Internet before addressing the complexity of a proxy device and all of its benefits and threats. Similar to your physical address, your IP address serves as an identifier of your location that other users may view and use to determine where to transmit the data you request. Your IP address is visible to other Internet users, who then send software, emails, or web pages to your device. The provider issues the IP address, and even while its primary usage is only beneficial, it may also be detected by hackers.
The term “proxy” is used to fake your computer’s IP address and means substitute. This is helpful if you want to access a website that has been prohibited (or is otherwise unreachable) or if you want to browse untrusted websites anonymously. A proxy server serves the same functions as a remote mailbox where you would place any letters or packages that you did not wish to receive at your home.
Web proxies are required as the demand for Internet connectivity in the workplace rшыуы to shield an organization’s internal network from outside dangers. Web proxies, also known as proxy servers, are a simple method of filtering the traffic between your computer and the Internet.
Larger firms generally employ web proxies when implementing network security for two reasons: to safeguard their private information and to enhance the functionality of their internal network. A web proxy is essential on a network because it safeguards the organization’s information resources by filtering out websites that could contain harmful code.
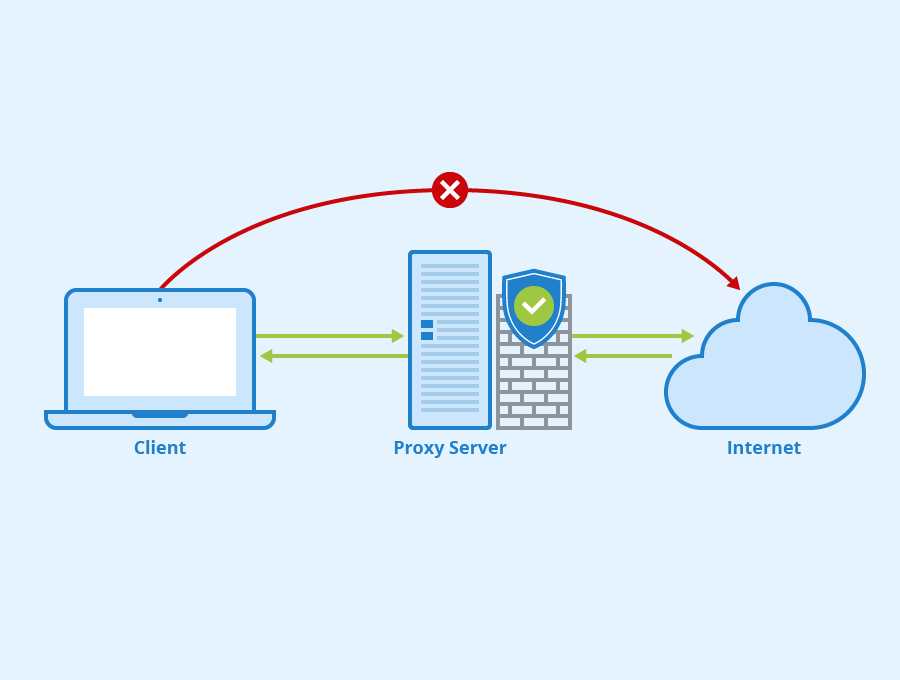
Given the possible expense of rebuilding an organization’s hardware once a virus renders it useless, this includes not only data but also physical assets. Businesses may have sensitive proprietary information, employee and customer personal information, and other data on their local network. Monitoring the security of your Internet use may not seem like much, but there is a lot of sensitive material that has to be secured.
Using a proxy could enhance performance by caching web pages, depending on the kind of proxy you are using and how it is set up. ProxyBros delivers a holistic and unbiased evaluation of proxy solutions and raises awareness of proxy technology and its opportunities. They delve into each proxy service, analyze, and test it to the bone, identifying the best proxies for diverse needs and purposes.
When your colleague accesses the same website later, the proxy server can provide that copy rather than requesting the original from the Internet by keeping a temporary duplicate of the page on its local server.
This is especially helpful for regularly frequented websites, such as the website of your business. Every time you come, this reduces the time it takes for the website to load. The majority of web proxy customers are huge companies or institutions that require a controlled method of keeping track of all of the network’s Internet users.
Proxy servers are used by both commercial businesses and academic organizations to safeguard their networks, although in slightly different ways. Using a proxy computer to access the Internet is practically the same as using a regular computer, with the exception that instead of connecting to the network directly, you use a local area network (LAN) to connect to another computer, which then allows you to access the Internet through its modem.
This is pretty simple on computers running Windows, macOS, or Linux. You simply go to the Internet settings menu, select the option that says “use a proxy server as LAN,” and input the IP address of the machine you wish to connect to. With smartphones and tablets, it is more challenging since you have to install third-party software and choose the proxy server you want to use from a list.
There are four different kinds of proxy servers, and each one has a different amount of secrecy and usage. We are discussing transparent proxies, reverse proxies, maximally anonymous proxies, and anonymous proxies.
Type 1: Anonymous
Anonymous proxies are the most prevalent kind of proxy server. They conceal the real IP address. Your home IP address will not be visible to the device making the connection, and if you want to increase security even further, you may encrypt the connection between your computer and the proxy server. Most people prefer this kind of proxy connection.
Type 2: Maximum Anonymous Proxy
Even greater privacy than a standard proxy is provided by the utmost anonymous proxy. This is because it impersonates a regular computer and sends one-way queries to the network, concealing the fact that it is a proxy. Because it is not a hub in this instance, the destination website or application does not subject it to the constraints that are in place for proxy servers.
Type 3: Transparent Proxy
A transparent proxy is used as a regular entry point that impersonates the device making the request, even if the majority of users do not believe this kind of proxy to be one at all. It is not used for the same objectives as the first two categories on our list because there is no anonymity present. It is primarily designed to allow many businesses to use the same address. Numerous “cloud” services that employ multiple computers but only display one IP address for them are built on such proxy servers.
Type 4: Reverse Proxy
The so-called reverse proxy is the final type of proxy on our list. The main goal of connecting through a server like this is to stop unauthorized users from accessing your computer, not to shield or mask you from accessing websites or apps. Individual apps are available for this kind of proxy server for people who keep sensitive data on their hard drive. In general, this is a standard proxy program created for big businesses with computerized corporate data. By using a reverse proxy connection, these businesses stop people from connecting directly to computers and instead divert those who do to a specific server that is guarded by a multitude of firewalls, encryption systems, and other measures.








